Our assessment tolls cover address major frameworks that are used as checklist when relevant.
For Roles and skills in Digital and in Cybersecurity.

Exclusively built for A&P.
And Solvay Lifelong Learning. 
For human skills and teams’ composition.
"We employ one of the highest number for certified assessors and analysts in Europe."
Raffaele Jacovelli, HTP group
For clients organisations, our credentials include :


For service organisations, our credentials include :




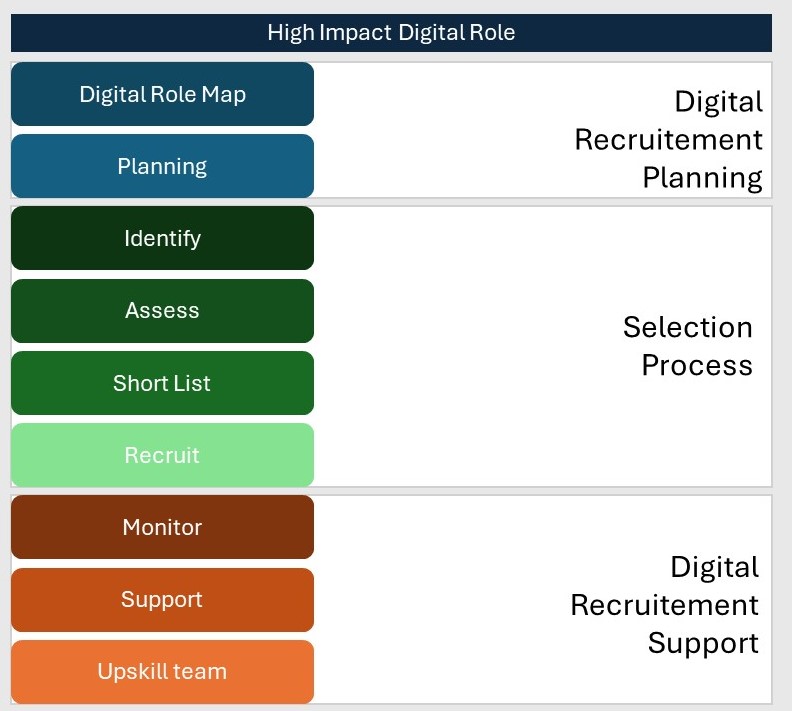
Advising and recruiting executives with expertise of Digital governance involves a combined mastery of human resources management and Enterprise Governance of Digital and IT. We also assisted our clients in restructuring and revamping their organisation structure, strategy and working methods based on the various frameworks that we adopt.
Some of those frameworks were co-developed by our founders :