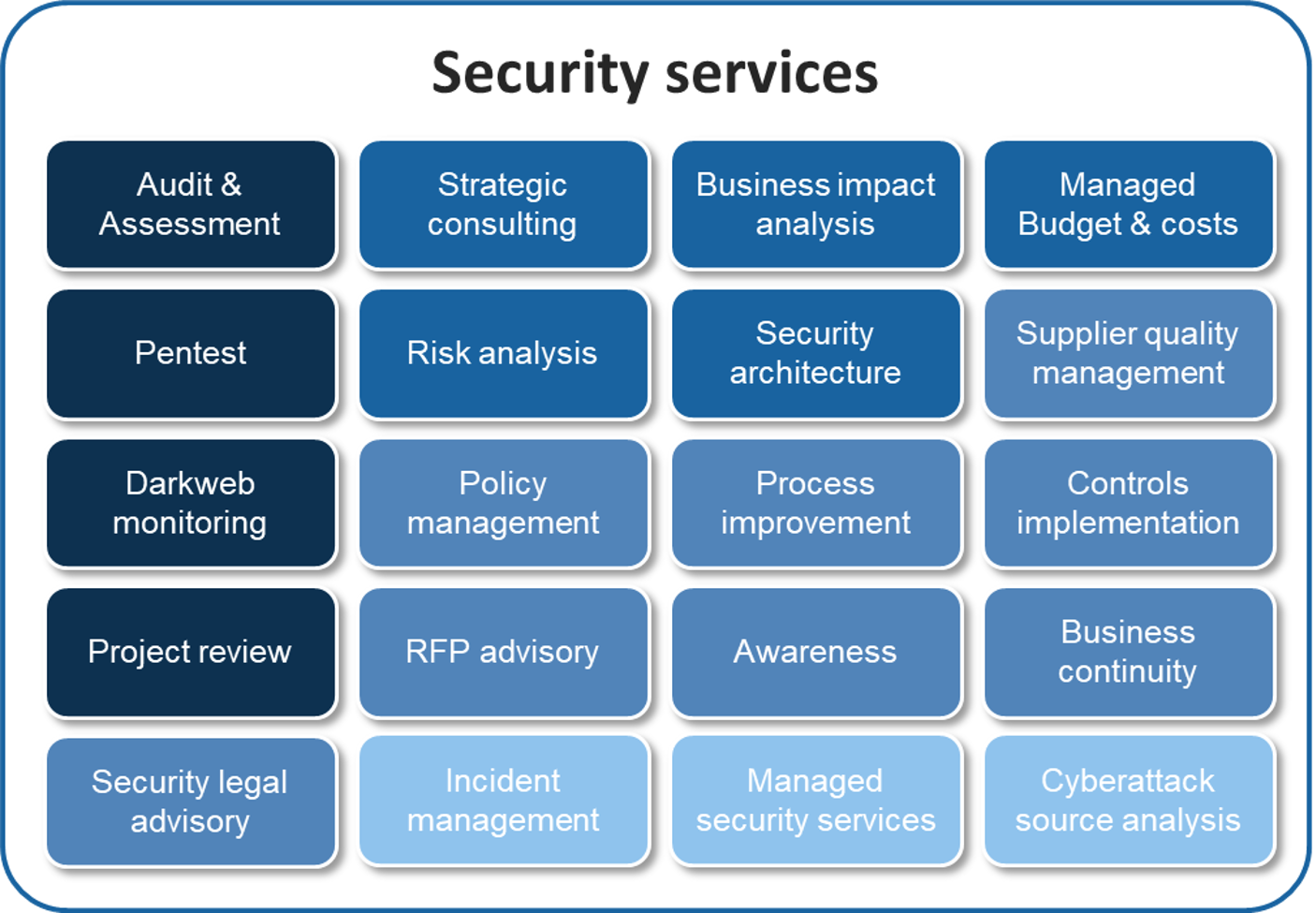
Business cases

Setting up effective IT governance within a government institution
Ataya & Partners recently collaborated with a major governmental institution to transform its IT governance using the COBIT framework...

Implementation of CISO As A Service and ISO27001 assessment in a Belgian public organisation